Published: Oct 17, 2025
Automating discovery of cryptographic assets
You can’t fix what you can’t see. For most organisations, the first challenge in preparing for post-quantum cryptography (PQC) isn’t algorithm selection, it’s visibility. Cryptographic assets are everywhere: in certificates, applications, APIs, and legacy systems. But many of them are hidden, poorly documented, or forgotten altogether.
In this article, you’ll learn why discovery is critical for PQC migration, why manual methods fall short, and how automation helps enterprises manage this complexity at scale.
Key takeaways
- Discovery is the foundation of PQC migration.
Without knowing where cryptography is used, migration plans risk being incomplete or misdirected. - Manual approaches are no longer feasible.
The sprawl of digital assets across hybrid environments makes spreadsheets and one-off audits ineffective. - Automation unlocks scale and accuracy.
With the right tools, organisations can continuously scan, map, and monitor cryptographic usage. - Visibility drives prioritisation.
Automated discovery provides the insight leaders need to decide what to protect first.
The hidden challenge
Most enterprises underestimate how pervasive cryptography is in their environment. Keys and certificates underpin almost every secure interaction, from customer logins to partner data exchanges. Yet IT leaders often lack a clear picture of where those assets live, how they are managed, or whether they are still secure.
Limited visibility into cryptographic keys and certificates creates operational blind spots that increase risk.
Why automation matters
Manual discovery methods, like one-off audits or asset inventories managed in spreadsheets, simply can’t keep up with the scale of modern enterprise IT. Hybrid and multi-cloud environments introduce new complexity, while shadow IT and legacy systems create blind spots.
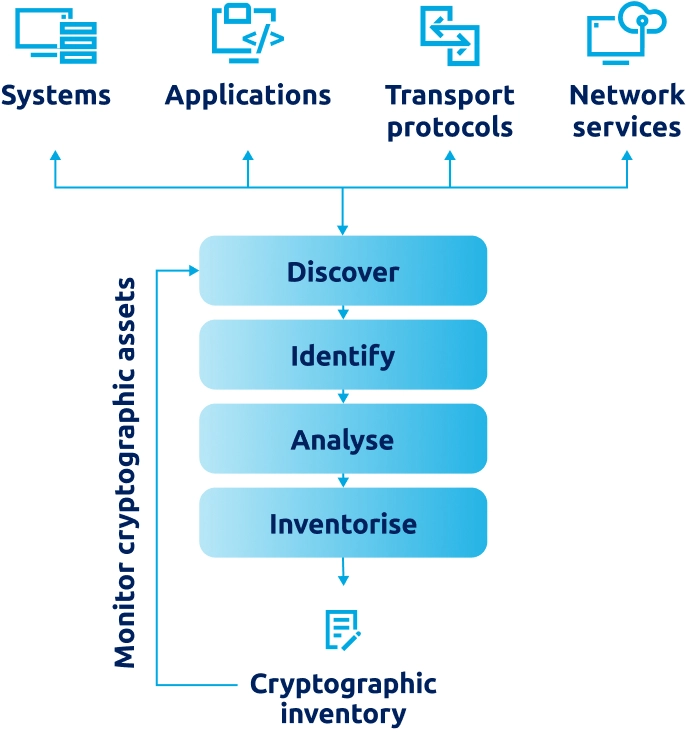
Figure 1: High-level architecture of an automated discovery of cryptographic assets.
Automated discovery changes the game. These tools can:
- Scan continuously across applications, APIs, and systems
- Identify algorithms and certificate lifecycles automatically
- Integrate with dashboards for compliance and governance reporting
- Alert teams when vulnerabilities or outdated assets are found
This visibility allows organisations to move from reactive firefighting to proactive planning.
From visibility to action
Discovery is not an end in itself, it’s what makes informed decision-making possible. Once cryptographic assets are mapped, leaders can:
- Prioritise systems that handle long-lived or sensitive data, such as healthcare or financial records.
- Replace vulnerable algorithms where they matter most.
- Strengthen governance by ensuring crypto policies are consistently enforced across the enterprise.
Automation turns visibility into control. It allows security and IT teams to act decisively, streamline operations, and prepare confidently for PQC migration.
Making the invisible visible
Discovery is the critical first move in any PQC migration. Without it, organisations are effectively navigating blind. With it, they can see clearly, prioritise confidently, and act decisively.
Automation doesn’t just make discovery faster; it makes it sustainable. Continuous visibility means businesses can adapt as standards evolve and threats change, ensuring long-term resilience.
At NCS, we help organisations take that first step toward quantum readiness.
By combining advanced automation tools with deep expertise in cryptographic management, we enable enterprises to uncover their hidden assets, strengthen governance, and build a clear foundation for PQC migration. With the right discovery strategy, every move that follows becomes smarter, safer, and more future-ready.
Make your next move toward PQC readiness
Continue the journey
In the next article, ‘Security validation of Quantum Key Distribution Networks’ sees how NCS validates advanced quantum-era security technologies in real-world conditions — moving from theory to proof of resilience.
Go back
Missed the big picture? Start with ‘Quantum-safe cryptography: When and how to start’ to understand why PQC matters and what a proactive migration roadmap looks like.
Go deeper
Download our comprehensive guide 'Preparing for a quantum-safe future'.
References
[1] World Economic Forum. Navigating Cyber Resilience in the Age of Emerging Technologies: Collaborative Solutions for Complex Challenges. October 2024.
[2] National Institute of Standards and Technology. NIST Special Publication 1800-38B. Migration to Post-Quantum Cryptography – Quantum Readiness: Cryptographic Discovery Volume B: Approach, Architecture, and Security Characteristics of Public Key Application Discovery tools. December 2023.
[3] National Security Agency. The Commercial National Security Algorithm Suite 2.0 and Quantum Computing FAQ. April 2024.