Published: Jul 14, 2020
shifting security left in application development
 The DevOps movement is about being able to deliver applications fast through automation, and having a shift left mentality where testing is performed earlier in the project lifecycle.
The DevOps movement is about being able to deliver applications fast through automation, and having a shift left mentality where testing is performed earlier in the project lifecycle.
As DevOps teams become more and more mature, concerns about testing, quality assurance and deployment are now being addressed earlier during the development process. But there remains one stumbling block which is preventing quick releases - security.
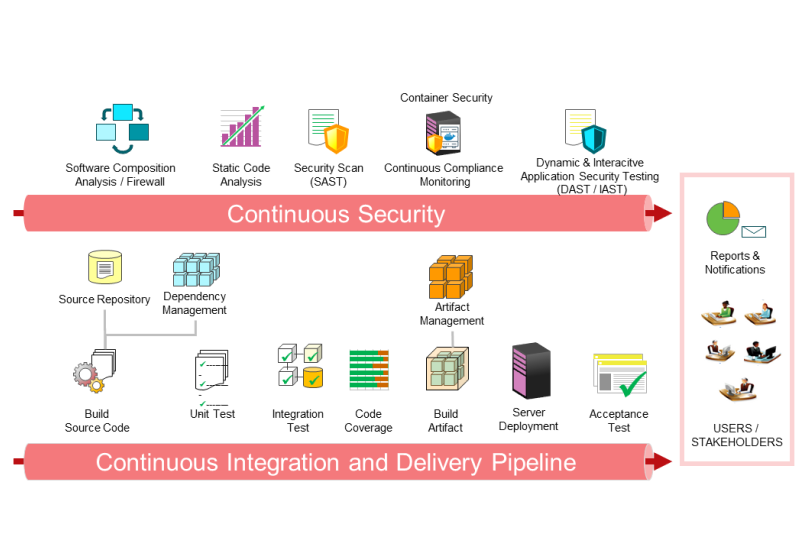
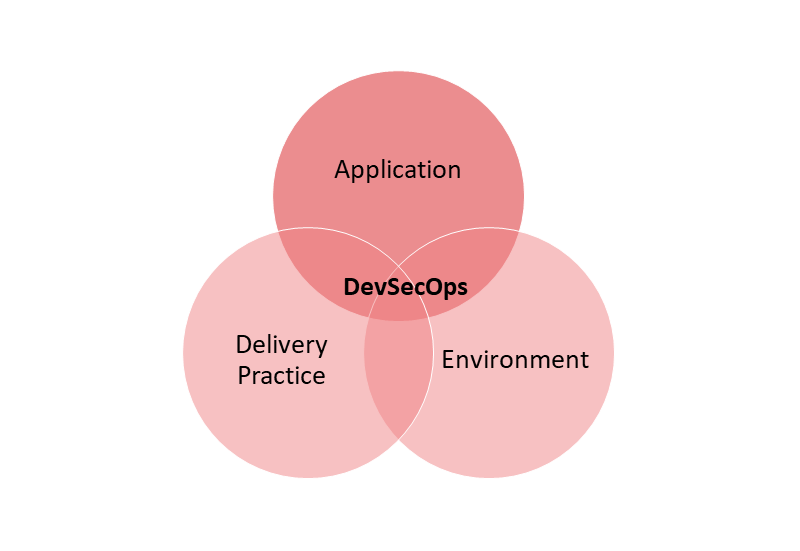
To address this, the next logical step is to embed security into DevOps. From secure development perspective, there are different aspects that need to be covered. These include delivery practice, application security, infrastructure controls, and monitoring to ensure that compliance is maintained throughout the phases of development and operations.
Below are some of the best practices that we would recommend for the design of a DevSecOps framework.
1. Embed security into the application development lifecycle
Whether you are using the agile or waterfall development model, it is good to practise secure coding by regularly scanning your code and open source libraries, at least on a daily basis. You have to do both the Code Quality Check and Static Application Security Testing using tools that can detect the top security issues identified by the Open Web Application Security Project (OWASP).
Scanning should not stop at the code level. You should also scan for vulnerabilities while doing unit and functional tests using Interactive Application Security Testing. A good tool should be able to follow the path of requests to any component of the application with full traceability to any vulnerabilities in the component.
Finally, it is also a good practice to simulate attacks and try to penetrate your application from your front-end service using a Dynamic Application Security Test tool.
Running all types of security testing in parallel with continuous integration lowers the risks of introducing vulnerabilities that could lead to security breaches.
2. Apply zero trust architecture
It is always a good idea to not allow any access to an application until the entity that is requesting access (device, user, system or application) is verified. Tighten verification by using token-based authentication, trusted certificates and multi-factor authentication.
3. Use “as-code” model on security
DevSecOps advocates the implementation of “security policy as code” which not only allows policies to be pushed out easily but also aids in monitoring compliance and maintaining (add, remove, update) policies. Using a configuration management tool to implement the “as code” approach will enable full automation and continuous compliance monitoring for environments including cloud, on-premises infrastructures and middleware.
Delivering secure-by-design applications with a shift-left approach to security